Ever since the Russian government launched an online disinformation campaign intended to disrupt the 2016 presidential election, it has been taken for granted that the Putin regime poses a major threat to the national security and welfare of the United States.
Yet what if an equally, or perhaps even greater threat, exists south of Russia's borders?
Vice President Pence certain thinks so, as he elaborated in a recent speech. And while Pence has been no better than the rest of the Trump administration when it comes to acknowledging the full scope of Russian meddling during the 2016 presidential election, his speech raised valid points about China's own corporate espionage and propaganda campaigns.
"As we speak, Beijing is employing a whole-of-government approach, using political, economic and military tools, as well as propaganda, to advance its influence and benefit its interests in the United States," Pence told the Hudson Institute in Washington, DC, as ABC News reported. While much of Pence's alarm-sounding is politically motivated — after all, this executive branch is infamously xenophobic — the proposition that China is covertly spying on U.S. corporations via embedded microchips is being widely reported, though many corporations who were targeted deny that they were affected.
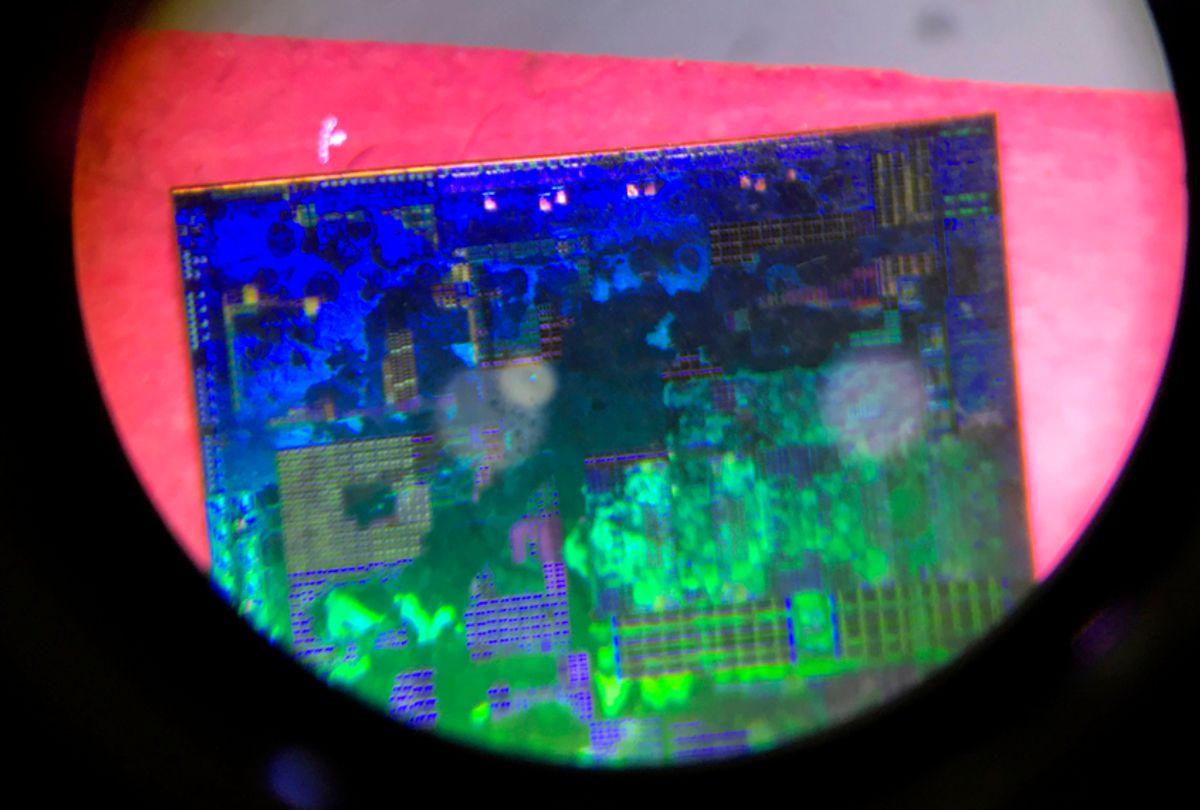
A recent report from Bloomberg explained how Chinese "spy" microchips have been installed in American products, with far reaching implications for America's corporate and governmental security:
There are two ways for spies to alter the guts of computer equipment. One, known as interdiction, consists of manipulating devices as they’re in transit from manufacturer to customer. This approach is favored by U.S. spy agencies, according to documents leaked by former National Security Agency contractor Edward Snowden. The other method involves seeding changes from the very beginning.
One country in particular has an advantage executing this kind of attack: China, which by some estimates makes 75 percent of the world’s mobile phones and 90 percent of its PCs. Still, to actually accomplish a seeding attack would mean developing a deep understanding of a product’s design, manipulating components at the factory, and ensuring that the doctored devices made it through the global logistics chain to the desired location—a feat akin to throwing a stick in the Yangtze River upstream from Shanghai and ensuring that it washes ashore in Seattle.
A government official who spoke to Bloomberg estimated that the microchips installed in the software of the company Supermicro had managed to affect nearly 30 companies, including Apple Inc., government contractors and a major bank. Three individuals described as "senior insiders at Apple" confirmed to Bloomberg that malicious chips were discovered on Supermicro motherboards in the summer of 2016, although Apple claims that when it severed ties with Supermicro in 2016, it was for unrelated reasons.
READ MORE: Beto O'Rourke & Martin O'Malley: the dark horse ticket that could beat Trump in 2020
Elemental Technologies, whose servers were assembled by Supermicro, was acquired by Amazon in September 2015; Amazon denies that Bloomberg Businessweek is correct in its reporting. "It’s untrue that AWS [Amazon Web Service] knew about a supply chain compromise, an issue with malicious chips, or hardware modifications when acquiring Elemental," Amazon wrote. Apple expressed a similar sentiment, claiming that "on this we can be very clear: Apple has never found malicious chips, ‘hardware manipulations’ or vulnerabilities purposely planted in any server." Meanwhile six current and former senior national security officials, working for both Presidents Barack Obama and Donald Trump, confirmed to Bloomberg that malicious microchips had been discovered and investigated, with one speculating that China's objective was to obtain high-value corporate secrets and access to sensitive government networks.
Lest you think China's efforts are limited to this implanting microchips in software used by Americans, check out this report from The Daily Beast:
One former CIA analyst put it bluntly: Beijing’s agents in this country aim “to turn Americans against their own government’s interests and their society’s interests.”
[...] Most Americans have never even heard of the main conduit of such influence, an obscure but sprawling Chinese Communist Party agency known as the United Front.
The organization has been around in one form or another since the World War II era. Mao famously referred to the United Front as one of the Communist Party’s “magic weapons.” These days, United Front operations sometimes resemble the CIA’s soft attempts to buy off, co-opt, or coerce influential community leaders. Sometimes it functions like a booster club for pro-party locals, or like an advocacy group trying to sway public opinion. Sometimes it works in concert with China’s traditional intelligence agencies, such as the Ministry of State Security, to gather information or apply pressure. And United Front networks may sometimes play a role in facilitating intellectual property theft and soft intelligence collection, though that role isn’t always clear.
What is clear is that the United Front is active in dozens of U.S. cities and has been for years, with almost no one the wiser.
Shares